
2021 Gmc Sierra 10-speed Transmission Problems, 2020 Silverado 1500 10 speed transmission issues, 7.87 MB, 05:44, 38,791, crkdtoes, 2021-01-25T22:55:06.000000Z, 19, New 2021 Cayenne Red Tintcoat GMC Sierra 1500 Crew Cab Short Box 4, www.taylorsautomaxbuickgmc.com, 960 x 540, jpeg, at4 denali buick yakima slt cayenne tintcoat peterson trim ritchey chateauguay daytona jerseyville elevation sle vin, 12, 2021-gmc-sierra-10-speed-transmission-problems, KAMPION
When users connect to this access point, all the data they share with the network passes through a server controlled by the attacker. An attacker can create an evil twin with a smartphone or other. What scenario describes an evil twin attack? Evil twin attack is just the beginning.
Once you’re connected via the hacker’s hot spot, they can use it to just clone your data, sure, but they can do a few more devious things as well. Having control of your data stream. Most often, the victims of such attacks are ordinary people like you and me. In linux, what command can be used for viewing and setting wireless voip interface parameters? Ifconfig iwconfig wlanconf wifid uestion 7 (1 point) what scenario describes an evil twin attack? Question 12 what scenario describes an evil twin attack? It is the wireless network equivalent of the phishing scam. I then followed the steps given below to launch the attack. The wireless card s name is wlan0.
Evil Twin Attack - Guide - Sudorealm

Lab – Hacking Wireless Network/s via Evil Twin Attack | Cybersecurity

Hacking WPA2 Wi-Fi password using Evil Twin Attack | DNSMASQ and

KNOW HOW TO PERFORM EVIL TWIN ATTACK

Wifiphisher Evil Twin Attack - kalitut

Wifiphisher Evil Twin Attack - kalitut

The Evil-Twin Framework: A tool for improving WiFi security
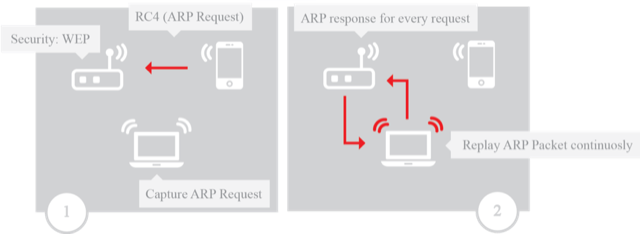
The Evil-Twin Framework: A tool for improving WiFi security
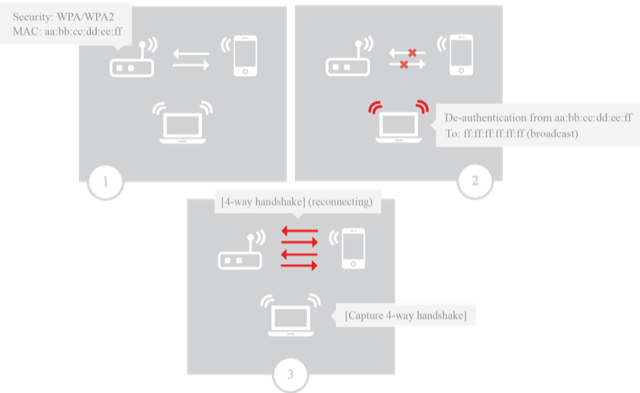
CWNA Chapter 16: Wireless Attacks, Don't Go Rogue - Techimike

The Infernal-Twin tool, easy hacking wireless networksSecurity Affairs

EmoticonEmoticon