
2021 Gmc Sierra 10-speed Transmission Problems, 2020 Silverado 1500 10 speed transmission issues, 7.87 MB, 05:44, 38,791, crkdtoes, 2021-01-25T22:55:06.000000Z, 19, New 2021 Cayenne Red Tintcoat GMC Sierra 1500 Crew Cab Short Box 4, www.taylorsautomaxbuickgmc.com, 960 x 540, jpeg, at4 denali buick yakima slt cayenne tintcoat peterson trim ritchey chateauguay daytona jerseyville elevation sle vin, 12, 2021-gmc-sierra-10-speed-transmission-problems, KAMPION
Which of the following best describes a rootkit? Software used for the collection of personal data; Software hidden on a computer for the purpose of compromising the system; Software that provides the originator with the venue to propagate;
Open 13+ pages which of the following best describes a rootkit analysis in google sheet format. Software hidden on a computer for the purpose of. The scenario describes a remote access trojan rat which is a type of malware that allows attackers to take control of systems from remote locations. Which of the following best describes a rootkit. Which of the following best describes spyware. Which of the following best describes the type of malware infecting this companys network. Question 25 which of the following best describes a rootkit? A destructive program disguised as a real program, like a screensaver a virus that changes its code as it delivers the infection a program that easily can hide and allow soeone to take full control of your computer from a remote location none of these. Which of the following best describes a rootkit?
Malware, Rootkits & Botnets A Beginner's Guide on Apple Books

Get Passleader Cisco 350-018 Brain Dumps And Study Guides With Low Cost

Malware, Rootkits & Botnets A Beginner's Guide - Free eBooks Download
Unlock your Full SY0-601 CompTIA Stable Exam

Unlock your Full SY0-601 CompTIA Stable Exam

Discovering Infected Systems | Get Certified Get Ahead

PPT - Malware PowerPoint Presentation, free download - ID:6234533

What Is A Backdoor And What Is It Used For Quizlet? - TimesMojo

CAS-003 Exam – Free Actual Q&As, Page 24 | ExamTopics
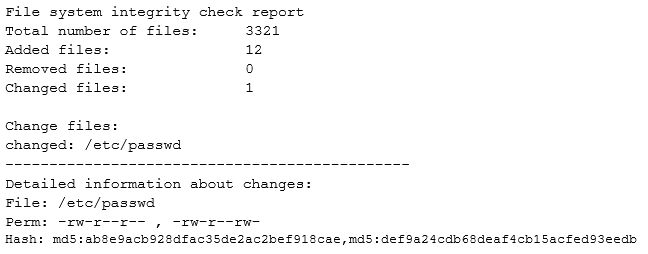
CIN506 MID-Semester paper.pdf - Department of Computer Science

EmoticonEmoticon